
Your phone calls are raining down from space right now. Someone with a backyard satellite dish could be listening. UC San Diego researchers showed this in late 2024 and finally went public in October 2025. Three months later, as 2026 begins, many critical systems are still only partially fixed.
Their $800 setup captured the numbers, call recordings, and texts of 2,700 T-Mobile customers in nine hours—broadcast in the clear, for anyone to intercept.
The $800 Weapon

The equipment isn’t exotic. A satellite dish ($185), mounting hardware ($140), a motorized antenna ($195), and a USB tuner card ($230). Researchers placed it on a university rooftop in La Jolla, California, and waited. Within hours, they’d intercepted military secrets, corporate credentials, and intimate personal communications.
This is the same technology sitting on millions of American roofs for television. Millions of people own the equipment needed to conduct mass surveillance from space.
Nine Hours, 2,700 Lives
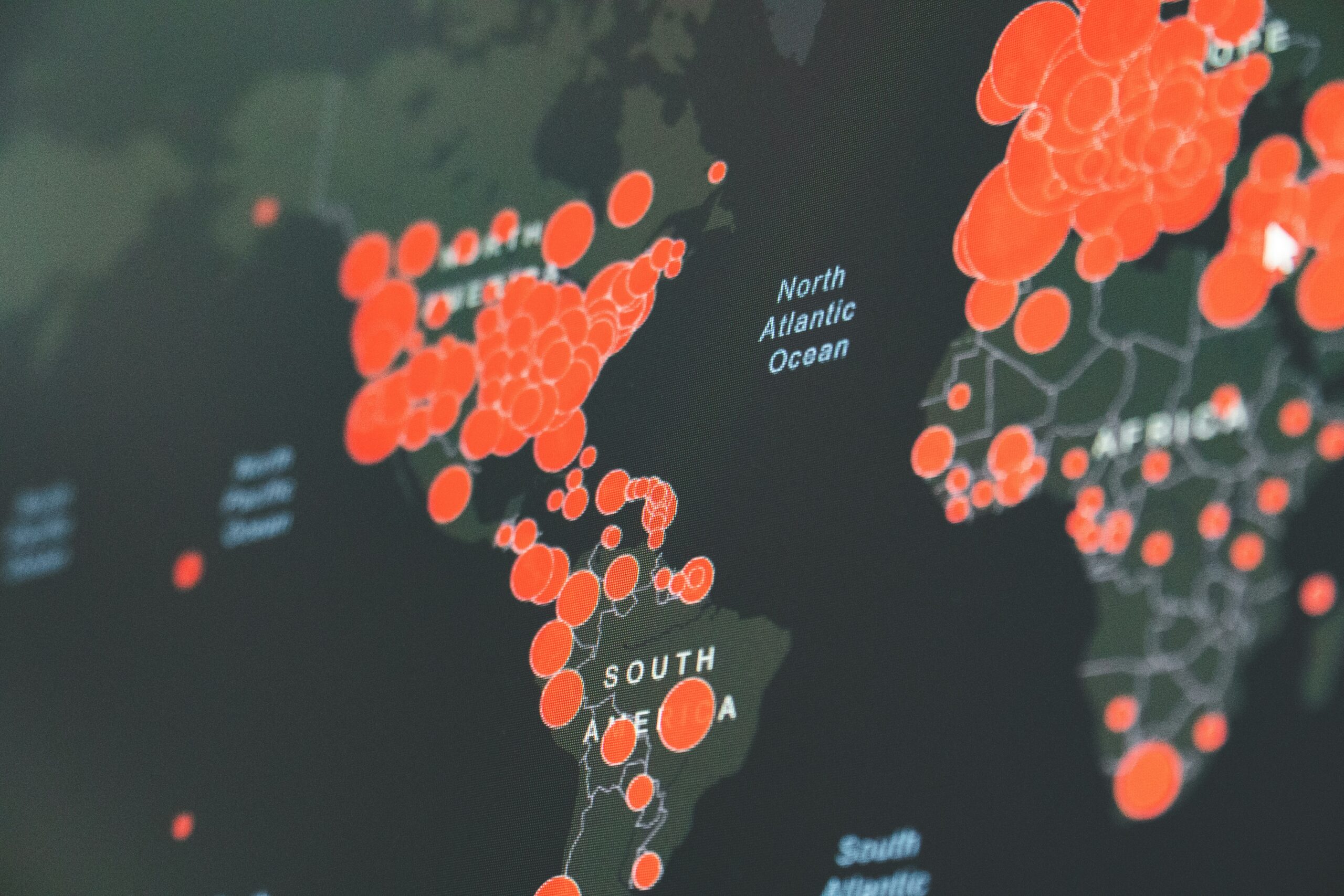
In a single nine-hour window, the equipment captured phone numbers and call content from 2,700 T-Mobile customers using satellite backhaul in remote areas. But researchers weren’t targeting civilians.
They were stunned by what else was revealed by those signals: the locations of US military vessels, Mexican military helicopter missions, corporate email servers with login credentials, power grid control systems, offshore oil commands, and passenger Wi-Fi from airlines.
Half The Sky Exposed

Here’s what wakes security experts at 3 a.m.: approximately 50 percent of all geostationary satellite signals carrying sensitive data operate completely unencrypted. Fifty percent. Half of the world’s military communications, financial transactions, and critical infrastructure commands broadcast openly.
Researchers examined 39 satellites and 411 transponders. They only scanned 15 percent of global geostationary satellites from San Diego.
Military Secrets From Space

US Navy vessel positions are transmitted unencrypted. Mexican military helicopters are broadcasting coordinates. Coast Guard operations. Law enforcement coordinating across borders. All accessible. The researchers documented vessel identities, communication protocols, and operational schedules.
Military strategists realized with horror that any nation with satellite capability—dozens of them—had been collecting this intelligence for years.
Mexico’s Power Grid Wide Open

Mexico’s Federal Electricity Commission serves 50 million people. Researchers found their internal communications completely unencrypted over satellites. Repair schedules. Grid vulnerabilities. Control system passwords. SCADA data.
An adversary could identify weaknesses, plan targeted attacks, and potentially blackout entire regions. Mexico’s critical infrastructure—electricity for millions—is exposed to anyone with a receiver.
Banks And Retailers Broadcast

Walmart Mexico. Santander Mexico. ATM networks. All are using unencrypted satellite links. Researchers captured login credentials, inventory data, financial transactions, and customer records. One compromised credential cascades across supply chains and financial institutions.
The scale of potential damage rippled through entire economic ecosystems. Hackers could have drained accounts. Criminals could have coordinated theft.
The Moment Of Horror

Dave Levin, University of Maryland professor leading the research, recalled: “When we saw all this, my first question was, did we just commit a felony? Did we wiretap?” They hadn’t. They were passively receiving signals broadcast openly to 40 percent of Earth’s surface.
The implication haunted them: if they found it so easily, who else had been listening? How many adversaries had already discovered this months or years ago?
The Entire Planet Broadcasts

Each geostationary satellite’s footprint covers approximately 40 percent of the Earth’s surface simultaneously. From Atlantic to Pacific. From North Africa to South America. One continuous beam carrying classified military data, corporate secrets, and personal communications.
Position a receiver in Europe and intercept various forms of intelligence. Move it to Asia and capture entirely different secrets.
The NSA Warning

The National Security Agency issued a cybersecurity advisory in May 2022, warning that most satellite links operate unencrypted, relying on “frequency separation or predictable frequency hopping” instead of encryption. The NSA knew. They warned the industry publicly. And nothing changed.
Three years passed. Companies ignored it. Agencies did nothing. The vulnerability remained overhead, humming silently, waiting for someone curious enough to look up and discover it.
Security Through Invisibility

Aaron Schulman, UC San Diego professor leading the research, explained the fatal assumption: “They assumed that no one was ever going to check and scan all these satellites and see what was out there. That was their method of security. They just really didn’t think anyone would look up.”
The entire satellite communications industry bet on invisibility rather than encryption. Hope that nobody checks. Pray that nobody cares. It’s security through wishful thinking.
Easier Than Stealing A Car

Matt Blaze, cryptographer at Georgetown University: “This was not NSA-level resources. These were DirecTV user-level resources. The barrier to entry for this sort of attack is extremely low.” Thousands of technically skilled people globally could replicate this.
Criminals. Foreign intelligence agencies. Hackers with a cause. All that is needed is $800 and a rooftop.
The Copycat Inevitability

Blaze predicted the cascade: “By the week after next, we will have hundreds or perhaps thousands of people, many of whom won’t tell us what they’re doing, replicating this work and seeing what they can find up there in the sky.”
Researchers faced a choice: hide the methods or force industry action.
T-Mobile’s Emergency Response

T-Mobile moved quickly after researchers notified the company in late 2024. Within weeks, T-Mobile encrypted all satellite backhaul communications and announced additional protections for customer signaling traffic.
The company emphasized the issue affected fewer than 50 cell sites out of 82,000 nationwide—a tiny fraction. T-Mobile could only prevent future breaches, not undo past exposure.
The Mixed Response

AT&T Mexico encrypted its links immediately. Walmart and Santander began remediation. However, when researchers conducted a follow-up scan in February 2025, they found that not all operators had taken action.
Some critical infrastructure owners have still not fully encrypted their satellite links—more than a year after being notified.
Enemies Already Listening

Intelligence agencies from Russia to China almost certainly exploited these unencrypted channels for years, researchers believe. Not just months—potentially a decade. They could have mapped U.S. military movements and tracked corporate expansion.
The question isn’t whether adversaries found this vulnerability. It’s: what did they do with what they found? What do they still possess?
Why Encryption Never Happened

Satellite operators understood encryption was needed. But bandwidth constraints, power limitations, vendor licensing costs, and legacy equipment compatibility created perfect inertia. Cost-benefit analysis suggested risk was low—nobody was looking, right?
Encryption required expensive upgrades. So they kept transmitting in the clear, betting on obscurity rather than cryptography.
Every Layer Must Encrypt

Application-level protection. Network-level encryption. Satellite beam-level, where available. Organizations must treat satellite links as unencrypted public wireless networks requiring multi-layered defense. Financial institutions need end-to-end encryption. Military systems need authenticated channels. Power grids need segmentation and monitoring.
The days of assuming satellite communications were somehow protected are finished. Encryption isn’t optional anymore. It’s the only sensible choice.
The Largest Breach Ever Revealed
This disclosure, made public last October, represents the largest documented exposure of unencrypted satellite communications ever revealed. Researchers estimate 85 percent of global satellite communications remain unexamined from their location—meaning vastly larger vulnerabilities exist worldwide.
Three months later, the industry faces a reckoning: encrypt everything or accept that adversaries are listening. There’s no middle ground.
Everyone’s Looking Now
For years, the satellite industry assumed nobody would look up. UC San Diego and University of Maryland researchers have proven that assumption to be catastrophically wrong. Since the October disclosure, governments are looking. Security agencies are looking. Adversaries are definitely looking.
The invisible highway overhead, once assumed to be secure, is now understood to be completely exposed. The question isn’t whether people will look up anymore. It’s: what will we do about what we find?
Sources
Don’t Look Up: There Are Sensitive Internal Links in the Clear on GEO Satellites
ACM SIGSAC Conference on Computer and Communications Security (CCS ’25), October 202
Satellites Are Leaking the World’s Secrets: Calls, Texts, Military and Corporate Data
Wired, October 13, 2025
Researchers find a startlingly cheap way to steal your secrets from space
CyberScoop, October 13, 2025
Researchers find Mexican satellite data is unencrypted, hackable
Mexico News Daily, October 16, 2025